
Check out the 15 different types of Password Cracking Techniques Used By Hackers. You should always be well aware of these types of attacks.
Putting up a good and long password is advised by cybersecurity, however, cybersecurity doesn’t teach us how to identify the hacking attempts. It doesn’t matter how strong your passwords were, there is always be an option for hackers to crack your passwords.
The hackers nowadays follow well-developed algorithms, which speeds up the processes to extract the passwords. So, if you are amongst those who think that putting up a tough password is not always enough, then this article is just for you.
15 Password Cracking Techniques Used By Hackers in 2020
In this article, we will discuss some password cracking techniques used by hackers to hack into our account. It’s worth noting that we have only shared the popular password-cracking techniques used by hackers, not all.
1. Dictionary Attack

A dictionary attack is a technique used by most of the regular hackers to determine the passphrase by trying their luck many times. Unlike its name, it works like a dictionary consisting of usual words that many people use as their password. On Dictionary attacks, hackers attempt to crack your passwords by making random guesses.
2. Brute Force Attack
Well, Brute-Force is an advanced version of Dictionary attack. In this attack, the hacker submits many passwords or passphrases with the hope of eventually guessing correctly. The attacker’s role is to systematically check all possible passwords and passphrases until the correct one is found.
3. Phishing

It is one of the easiest methods used by hackers. It does nothing, it simply asks users for their passwords but the process of asking password is unique and different. To carry out a Phishing campaign, hackers creates a fake page and asks you to log in with your Id and password. Once, you have entered the details, your details are transferred into the hacker’s server.
#4 Trojans, Viruses, And Other Malware

These programs are usually developed by hackers for the sole purpose of generating the target destruction. Viruses and worms are usually added to a user’s system so that they can make the full use of a machine or a network as a whole, and are usually spread by email or either it is hidden in any applications.
#5 Shoulder Surfing

Well, Shoulder surfing is the practice of spying on the user of a cash-dispensing machine or another electronic device in order to obtain their personal identification number, password, etc. As the world is getting smarter, Shoulder Surfing technique is becoming less effective.
6. Port Scan Attack

This is a technique often used to find weaknesses on a given server. It is normally used by those who are responsible for security to find vulnerabilities in the system. Port Scan Attack is used to send a message to a port and wait for a response and the received data from the open port is an invitation for hackers to hack into your server.
7. Rainbow Table Attack
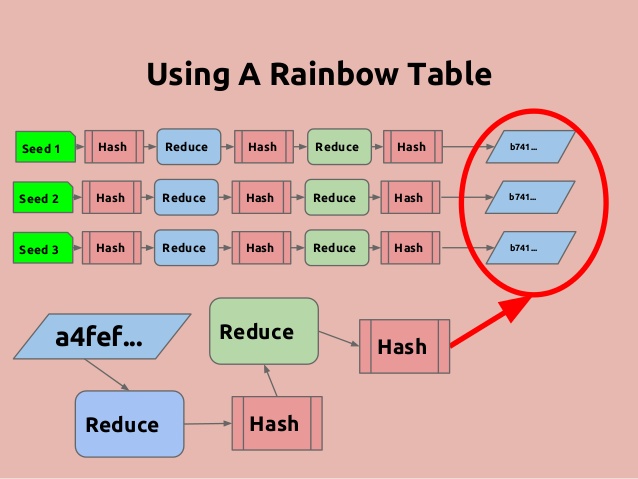
Well, Rainbow Table is usually a large dictionary which contains loads of pre-calculated hashes and the passwords from which they were calculated. The major difference between Rainbow and other dictionary attacks are the Rainbow table are specially optimized for hashes and passwords.
8. Offline Cracking

It’s one of the widely used password cracking techniques of hackers. In this attack, the hacker attempts to recover one or more passwords from the browser cache file. However, in Offline Password cracking, the hacker needs to have a physical access to the target computer.
#9 Social Engineering
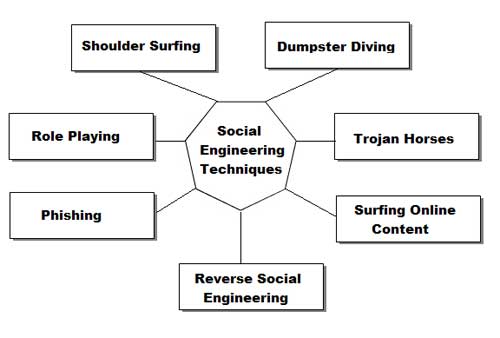
Social engineering is an attack that relies heavily on human interaction and often involves tricking people into breaking normal security procedures. Hackers can try different tricks to break into normal security procedures.
10. Guessing

Here hackers try to guess your passwords, they can even attempt to guess your security answer. In short, hackers can try to guess everything to break your security and hack your account. However, thanks to two-step verifications, this type of technique are usually a failure nowadays.
11. Hybrid Attack
Well, the hybrid attack is another well-known hacking technique that is widely used by hackers. It’s the blend of the dictionary and brute force attack. In this attack, hackers add numbers or symbols to the filename to successfully crack a password. Most of the people change their passwords by simply adding a number to the end of their current password.
12. Cracking Security Questions
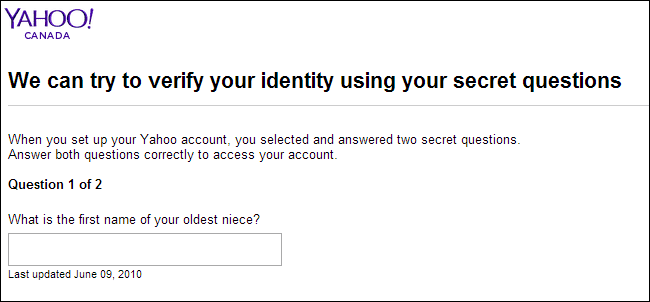
Well, we all now set up a security question on our Social networking platform. Security questions are useful when you can’t remember that one password. So you click on the ‘forgot password’ and there you need to answer the security question to reset your password. However, hackers also try to guess security questions. Well, we should always remember the fact that security question answers are something that is easy to remember and has personal meaning to you. So, if the hacker is your friend or relative, he/she can easily guess the security answer.
13. Markov Chains Attacks

It’s one of the most dangerous password cracking techniques used by hackers. In Markov Chains Attacks, hackers assemble a specific password database. They first split passwords into 2 to 3 long character syllables and then develop a new alphabet. So, the technique mainly relies on matching different sets of passwords until it finds the original password. It’s pretty much similar to the dictionary attack, but it’s much more advanced than that.
14. Hybrid Dictionary
This one is the result of both Dictionary and brute force attacks. It first follows the rules of dictionary attack in which it takes the words listed on the dictionary and then combines then with brute force. However, the Hybrid Dictionary attack takes a longer time to complete because it tries every dictionary word. The hybrid dictionary is also known as a Rule-based dictionary attack.
15. Spidering

It is another method which is used by hackers to crack passwords. Again, the spidering attack depends on brute force. On spidering, hackers grab all informational words that were connected to the business. For example, hackers use the words that are connected to the company like competitors website names, website sales material, studying corporate, etc. After grabbing those details, they execute a brute force attack.
16. Keyloggers

Well, Keyloggers are the famous threat in the security world. Keyloggers are the type of trojan horse that logs everything that you type through the keyboard including the passwords. The worst thing about keyloggers is that there are plenty of keyboard-logging hardware devices available on the internet which can record every keystroke. So, Keylogger is another password cracking technique that is widely used by hackers.
17. Password Reset

Nowadays, hackers find it much easier to reset passwords than to guess them. Hackers usually get around the typical Windows Protections and they use a bootable version of Linux to mount the NTFS volumes. By mounting NTFS Volumes, it helps hackers to locate and reset the admin password. Just think for a moment that you have forgotten the Windows Password, you can easily recover it through Microsoft account or through Command Prompt. The same thing hackers do to hack into the systems.
So, these are some of the popular password-cracking techniques used by hackers. I hope this article helped you! Share it with your friends also.
The post 15 Password Cracking Techniques Used By Hackers in 2020 appeared first on Tech Viral.
ethical hacking,hacking,bangla ethical hacking,bangla hacking tutorial,bangla tutorial,bangla hacking book,ethical hacking bangla,bangla,hacking apps,ethical hacking bangla tutorial,bangla hacking,bangla hacking pdf,bangla hacking video,bangla android hacking,bangla hacking tutorials,bangla fb hacking tutorial,bangla hacking book download,learn ethical hacking,hacking ebook,hacking tools,bangla ethical hacking course, tricks,hacking,ludo king tricks,whatsapp hacking trick 2019 tricks,wifi hacking tricks,hacking tricks: secret google tricks,simple hacking tricks,whatsapp hacking tricks,tips and tricks,wifi tricks,tech tricks,redmi tricks,hacking trick paytm cash,hacking trick helo app,hacking trick of helo app,paytm cash hacking trick,wifi password hacking,paytm cash hacking trick malayalam,hacker tricks, tips and tricks,pubg mobile tips and tricks,tricks,tips,tips and tricks for pubg mobile,100 tips and tricks,pubg tips and tricks,excel tips and tricks,google tips and tricks,kitchen tips and tricks,season 2 tips and tricks,android tips and tricks,fortnite tips and tricks,godnixon tips and tricks,free fire tips and tricks,advanced tips and tricks,whatsapp tips and tricks, facebook tricks,facebook,facebook hidden tricks,facebook tips and tricks,facebook latest tricks,facebook tips,facebook new tricks,facebook messenger tricks,facebook android app tricks,fb tricks,facebook app tricks,facebook tricks and tips,facebook tricks in hindi,tricks,facebook tutorial,new facebook tricks,cool facebook tricks,facebook tricks 2016,facebook tricks 2017,facebook secret tricks,facebook new tricks 2020,blogger blogspot seo tips and tricks,blogger tricks,blogger,blogger seo tips,blogger seo tips and tricks,seo for blogger,blogger seo in hindi,blogger seo best tips for increasing visitors,blogging tips and tricks,blogger blog seo,blogger seo in urdu,adsense approval trick,blogging tips and tricks for beginners,blogging tricks,blogger tutorial,blogger tricks 2016,blogger tricks 2017 bangla,tricks,bangla tutorial,bangla magic,bangla motivational video,bangla tricks,bangla tips,all bangla tips,magic tricks,akash bangla tricks,top 10 bangla tricks,tips and tricks,all bangla trick,bangla computer tricks,computer bangla tricks,bangla magic card tricks,ms word bangla tips and tricks,bangla computer tips,trick,psychology tricks,youtube bangla,magic tricks bangla,si trick Credit techviral

0 Comments